Cybercrimes — including hacking, phishing, and malware — aim to access your sensitive personal financial information in order to steal money from you or in your name.
Cybercrime is always a threat in this information age, but there are also some simple ways to keep your information and your money safe. With the tips below, you can protect yourself from online criminals.
Avoid Links
Just because an email seems to be from a source you know, doesn’t mean it’s the real thing. When you receive an email that looks like it’s from your bank, credit card company, or favorite online retailer, don’t click on links in the email. Instead, start a new session on that company’s website. Scammers try to trick you with phony email links, so you’ll type your login information into their fake page, giving them access to your real accounts. If you have doubts about the true source of an email, you can always call the company directly to make sure it’s real.
Protect Your Computer
Install reliable antivirus and anti-malware software on your home computer and be sure to update that software as new threats arise. Run scans regularly to detect any spyware or malware that may be lurking in the background to capture your personal financial information.
Secure Your Mobile Devices
Your smartphone or tablet come with strong protections, but their portability also makes them vulnerable. Never enter your personal information when you’re on a public Wi-Fi network, since hackers may be watching. Don’t download mobile apps unless you trust the source. Be sure to password-protect your devices just in case they get lost or stolen. You don’t want a stranger getting access to your financial accounts.
Browse Carefully
Only enter your personal information on a website if you know it’s secure. How do you know if it’s a secure site? The web address may start with “https” instead of the usual “http,” or you may see a little lock symbol at the beginning of the address bar. If you don’t see those security signs, your information may be vulnerable to theft.
Beware of Callers
No reputable financial organization will ever ask you for your password or other personal information over the telephone. If someone who claims to work for your bank or credit card company asks for that information, hang up on them. You can then look up the company’s real number and call them to verify. They’ll want to know if someone has been impersonating them on the phone! The same goes for email — don’t trust a message asking you to send personal information electronically.
Strengthen Your Passwords
It’s tempting to use one memorable password for all your online accounts, but that leaves all your accounts vulnerable if one of the companies experiences a breach. Instead, choose strong passwords for each account and change them often. You may need to use a program or browser extension to create and remember many different passwords for you.
Watch Your Accounts
Most financial companies have fraud-detection procedures in place, but that shouldn’t stop you from monitoring your accounts personally. Keep an eye out for unusual transactions, or ones you don’t remember making. Get in touch with the company as soon as you see anything unusual. The faster you catch the problem, the easier it is to fix.
Keep Your Software Up to Date
Did you know that older versions of Windows (XP, Vista, 7, or 8) and Internet Explorer are no longer supported by Microsoft? If you’re using these products, you could be putting your information at risk. Unsupported software is vulnerable to new cyber-attacks that can lead to loss of data on your computer, identity theft, stolen online banking credentials (username/password etc.) or a number of other negative outcomes. Some of these threats can even use your computer to launch more attacks on people you know or even the general public. Due to these serious risks, you should seriously consider upgrading to a computer running a supported version of Windows (10 or 11) with the most up to date version of Microsoft Edge as soon as possible.
Keeping software up-to-date to protect yourself extends outside of Microsoft products as well. Always ensure that you keep all software running on your computer updated as these applications can also be exploited if left unpatched. This includes applications such as Adobe Acrobat Reader, Oracle Java, and third party Internet browsers (ex. Google Chrome and Mozilla Firefox.) It is also highly recommended that you install and keep up-to-date anti-virus or anti-malware software that has an auto-protect feature.
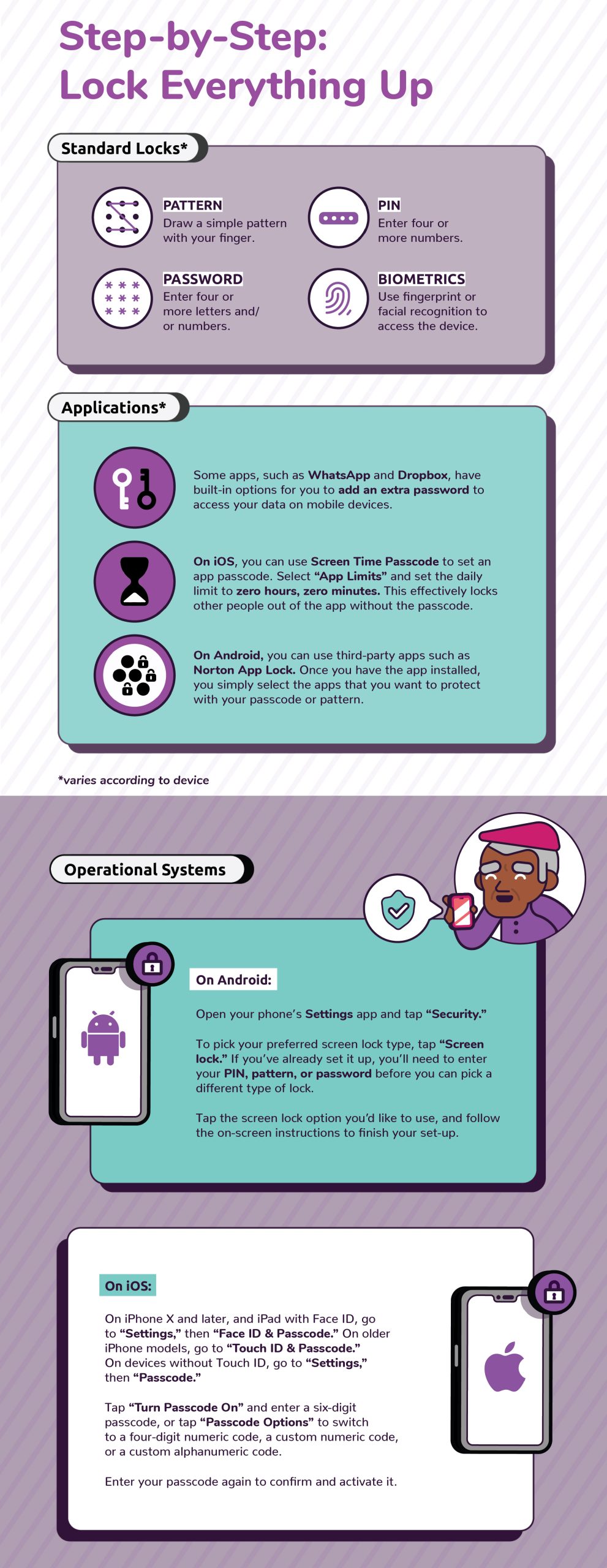
Lock Up Your Devices
(Click image to enlarge)
Source: KnowBe4
At BayCoast Bank, we work hard to keep your personal financial information safe and secure.
Please contact us whenever you have concerns or questions, and we’ll work with you to resolve your issue.
You can also view our resources page online, to get helpful information on cyber security, internet and email security, tips to prevent identity theft, and more.
See below for a collection of guides and information pertaining to cybersecurity.
Helpful Guides
- A CyberSecurity Guide for Businesses
- A CyberSecurity Guide for Financial Institution Customers (Consumers)
- FDIC Consumer News – A Bank Customer’s Guide to CyberSecurity: What Consumers Can Do … and What Banks and Regulators Are Doing … to Help Prevent Online Fraud and Theft
- Internet Security & Safety Tips
Important Contacts
- FDIC.gov
- FTC.gov – Federal Trade Commission
- OnguardOnline.gov
- IdentityTheft.gov
- FBI.gov
- Experian.com
- Transunion.com
- Equifax.com
- StaySafeOnline.org
Common terms pertaining to cybersecurity.
Malware
Short for “Malicious Software,” malware refers to software programs designed to damage or do other unwanted actions on a computer system. Common examples of malware include viruses, worms, trojan horses, and spyware.
Viruses, for example, can cause havoc on a computer’s hard drive by deleting files or directory information. Spyware can gather data from a user’s system without the user knowing. This can include anything from web pages a user visits to personal information, such as credit card numbers.
Consumers can combat malware by installing anti-virus and anti-spyware utilities that will seek and destroy malicious programs. Anti-virus and anti-spyware can be purchased wherever computer products are sold.
Phishing
There is a new type of Internet piracy called “phishing.” In a typical case, you will receive an e-mail that appears to come from a reputable company that you recognize and do business with, such as your financial institution. In some cases, the e-mail may appear to come from a government agency, including one of the federal financial institution regulatory agencies. In a “phishing” scam, you could be redirected to a phony website that may look exactly like the real thing. Once inside that website, you may be asked to provide your Social Security Number, account numbers, passwords, or other information used to identify you. When you provide this information, those perpetrating the fraud can begin to access your accounts or assume your identity. Never reply directly or click on a link in response to an e-mail that asks for your personal or financial information. Remember – your bank will never contact you “out of the blue” to ask for personal financial information.
Do not respond to e-mail that may warn of dire consequences unless you validate your information immediately. Contact the company to confirm the e-mail’s validity using a telephone number or web address you know to be genuine.
When submitting financial information to a website, look for the padlock or key icon at the bottom of your browser, and make sure the Internet address begins with “https.” This signals that your information is secure during the transmission.
Use anti-virus software and keep it up to date. Anti-virus software and a firewall can protect you from inadvertently accepting unwanted “key-logger” files. Look for anti-virus software that recognizes current viruses as well as older ones.
Keep your computer’s operating system up to date and download security patches. These patches for your operating system close holes that “hackers” or “phishers” could exploit.
Smishing
Similar to phishing, smishing uses cell phone text messages to deliver the bait to get you to divulge your personal information. The hook (the method used to actually “capture” your information) in the text message may be a website URL, however it has become more common to see a phone number that connects to an automated voice response system.
The smishing message usually contains something that wants your “immediate attention”. Some examples include:
1. “We’re confirming you’ve signed up for our dating service. You will be charged $2/day unless you cancel your order on this URL: www.?????.com.”
2. “(Name of popular online bank) is confirming that you have purchased a $1500 computer from (name of popular computer company). Visit www.?????.com if you did not make this online purchase.”
3. “(Name of a financial institution): Your account has been suspended. Call xxx-xxx-xxxx immediately to reactivate.”
The hook may be a legitimate looking web site that asks you to enter your personal financial information, such as your credit/debit card number, CVV code (on the back of your credit card), your ATM card PIN, SSN, email address, and other personal information. If the hook is a phone number, it normally directs to a legitimate sounding automated voice response system, similar to the voice response systems used by many financial institutions, which will ask for the same personal information.
Do not respond to text messages, website addresses or telephone numbers that may warn of dire consequences unless you validate your information immediately. Contact the actual company to confirm the validity of the request using a telephone number or web address that you know to be genuine.